Framework 144 Using Cyber Security Governance Principles
Introduction
The Australian Institute of Company Directors, in conjunction with the Cyber Security Co-operative Research Centre, has developed 5 principles with 10 key questions to help organisations proactively tackle oversight and management of cyber risk; develop cyber resilience to be prepared for any significant cyber incident. Cyber incidents can involve unauthorised activities in your networks, generally for financial or strategic gain. Threats can come from individuals, issues-motivated groups, criminal syndicates, state-sponsored groups, etc.
Theft of organisational data has emerged as a key cyber threat; other disruptions can occur to critical infrastructure or essential services and supply chains; both small and large organisations can be targeted;
"...healthcare, food distribution, financial services and energy sectors are key targets domestically and internationally..."
AICD et al, 2022.
These principles and key questions can be used as a part of a transformation effort
Five principles
1. Set clear roles and responsibilities (this involves
- defining and recording clear roles and responsibilities for building effective cyber resilience at all levels of the organisation, including a cyber champion who is to promote cyber resilience and answer questions; be continually updated as situations, organisational structures, staff, technology, etc change
- there should be a shared enterprise-wide responsibility for cyber risk, not just with the IT team
- comprehensive and clear reporting systems at all levels in the organisation from the Board downwards about emerging trends, threats, risks, etc, ie a holistic picture of the organisation's cyber posture and risk profile; include performance of cyber strategy, progress of key initiatives, misuse of data, data breaches, etc. Some common metrics:
"...i) cyber incident detection, prevention and response, including incident trend analysis
ii) cyber strategy performance, key initiatives and progress to date
iii) staff-related instances, such as staff accessing or misusing data are in breach of policies
iv) internal audit activities, including outcomes of vulnerability and threat assessments
v) external party assessments, including penetration testing results and benchmarking against peers and international standards
vi) staff cyber training rates and completion
vii) phishing exercise results
viii) assessing of the broader threat environment, formed by vendor alerts, ASSC alerts and intelligence shared by other organisations, and response to threats..."
AICD et al, 2022
- using independent external experts to complement your internal expertise, ie auditing (internal and external) as part of understanding vulnerability and threat assessments; an audit can provide information on how your organisation measures up against international standards, ie indication of your organisation's cyber risk maturity which is an important input for developing the organisation's cyber risk strategy and cyber risk controls; while compliance to a particular industry standard is important, it shouldn't allow complacency about future threats; despite external experts being a valuable source of assistance, need to be cautious about being too reliant on them; factors for assessing within external cyber audit and benchmarking:
"...i) regulatory and standards compliance: does the organisation meet its domestic legal and regulatory requirements? Is data or information covered under privacy provisions stored appropriately? How does the organisation align to or compare with to key standards frameworks?
ii) data stock take and access: what is the key data that the organisation collect and stores? Who, and what partners, have access to this data? Is data or information stored appropriately, including consistency with the regulatory obligations? Does the organisation regularly undertake a thorough data stock take to question whether all information needs to continue being held? is there an overarching data governance strategy that covers from creation to destruction?
iii) technical compliance: what software systems are used and how are they kept up to date? Is there a process for safely disposing of legacy systems and all data? Are there authentication systems in place? What controls ensure third parties cannot access internal systems without appropriate security measures? Are there logs of key systems so there is a record of who accessed what data?
iv) continuous improvement: do core security measures align with best practice? Are there systems in place to deal with the contemporary threat landscape?
v) awareness of threats: what alerts for monitoring are in place the flag threats and breaches or respond to critically patching alerts? Are staff trained to respond appropriately and in a timely way?
vi) governance and strategy: what are the systems and processes in place to manage and mitigate risk, or respond to threats or real events? How do individual responsibilities fall in each team? What approvals would they require, and to whom would they report?
vii) overall risk assessments: how does the level of resilience across the organisation compare against industry peers in the context of alignment with standards and testing results? How does this resilience and risk posture align with the risk appetite of the cyber strategy of the organisation?..."
AICD et al, 2022
- collect data where possible on the effectiveness of cyber risk practices, ie cyber incidents detection; prevention and response plus incident trend analysis; penetration testing and benchmarking against others, etc.
- encourage regular formal and informal working groups of key staff to meet regularly to discuss cyber risk and associated matters, and to ensure coordination across different parts of the organisation.
Areas of concern
- cyber risk and strategy not being key items in meeting agendas, but only feature periodically
- not regularly reviewing skills, technologies, etc to check if adequate to handle cyber security risk
- too much focus on technical solutions in cyber threats
- too much jargon in communications about cyber risk
- limited checking or reviewing or auditing by external cyber experts
- no clear lines of management responsibility for cyber security.)
2. Develop, implement and evolve a comprehensive cyber strategy (this involves
- a proactive cyber strategy that identifies opportunities for the organisation to build cyber resilience; strategy that is appropriate for the size and complexity of the organisation, eg its IT infrastructure systems, its key personnel and core competencies, the type and nature of information held, stakeholders' expectations (including regulatory and contractual obligations)
- identify key digital assets (including data), processes (eg technological infrastructure, physical assets) and people, ie who has access to them, as the core to understanding and enhancing cyber capability; understanding how to comprehensively protect your digital assets to reduce reputational damage and/or operational performance; some key questions to assess where cyber vulnerabilities may exist:
"...1. Who has internal responsibility for the management and protection of our key digital assets?
2. Who has access for decision-making rights to our key digital assets? For example, can all customer-facing staff access and change key databases?
3. What access to key digital assets is provided to third parties?
4. Where are our key digital assets located? Is this still appropriate given the identified size of the risks?
5. What is the role of external suppliers in hosting and managing key digital assets?
6. What is the impact of the loss or compromise of any of our key digital assets..."
AICD et al, 2022
- role of insurance, ie it can provide a measure of protection in the event of losses from a critical cyber incident; often high cost and/or restricted or tailored coverage can reduce the appropriateness of insurance; extra advantages of insurance include
i) can be access to expert advice (usually engaged by insurer) in the event of a significant cyber attack
ii) process involved in providing background information for an insurance policy, it can provide a check on the degree of organisation's cyber resilience, ie
"...As the questions asked by the brokers/insurers will sometimes reveal previously unknown vulnerabilities..."
AICD et al, 2022
- understand the importance and potential risks of third-party users like suppliers; need to conduct due diligence on key external providers as they themselves can suffer significant cyber incidents that can impact your organisation, ie need
"...Sufficient visibility of the key third-party suppliers, what key digital assets and data they manage or host and what risk controls are in place and, importantly, a direct communications channel if they need to notify the organisation of a data breach or issue......The organisation more broadly has the appropriate internal capabilities and risk-management processes in place to appoint and monitor key external providers. This includes understanding the extent of an organisation's dependence on a provider's service. What data a provider may hold or have access to, the jurisdiction of not just the provider of where they will store the organisation's data, and any vulnerabilities associated with the arrangements that may exist......Have a clear understanding of, or criteria for, what cyber-resilient practices there should be in place to provide confidence ..."
AICD et al, 2022
- encourage information sharing and collaboration with regulators and industry peers on cyber challenges
- strategy must be designed to protect, respond and reactivate (this means regularly testing frameworks for regular control and uncontrolled outrages, eg penetration tests, white box exercises, internal audit, etc; appropriate use of online templates; ensure physical back-ups of key data and systems are really updated and securely stored; maintain off-line lists of who can assist during a cyber security incident and which key stakeholders to communicate with)
- part of the strategy includes a cyber incident response plan to help the organisation respond effectively, ie staff at all levels of the organisation need to have a clear understanding of their respective roles and responsibilities.
NB "...significant cyber incidents can be incredibly complex with a high number of variables that make comprehensive planning challenging..."
AICD et al, 2022
Key elements of a response plan include
i) responsibilities (set out the business functions and key personnel responsible for implementing the steps in the plan; best to have a cross-section of the organisation represented plus any suitable third-party external experts, not just IT, etc)
ii) resources (adequate resources available to handle the situation, eg physical resources like computer assets; data backups, etc; key internal expertise like cyber security, legal, operational, management, etc; external expertise and support like crisis advisors; legal advisers; cyber insurer support; communications support, etc)
iii) triage an immediate response (identify cyber incident is happening and assess its severity - impact of business operations, key stakeholders, etc; understand if external stakeholders need notification such as law enforcement agencies, insurers, regulators, etc)
iv) containment and eradication (as each situation is different, strategies differ due to the nature of the incident; sometimes affected areas can be taken off-line or isolated to prevent the spread of malware)
v) communications (in addition to staff and impacted customers, communicate with law enforcement agencies, regulators, media, etc plus broader public, etc; need to be clear who will be responsible for communicating with which stakeholder.
NB "...Cyber instances tend to be fast moving and very dynamic. While the incident itself can be damaging, how on organisational handles can be just as damaging to the ongoing reputation..."
AICD et al, 2022)
vi) recovery (need to address what is required once the immediate crisis has passed.
"...Steps for not only rebuilding systems and infrastructure, including your investment in IT systems if necessary, but also for examining 'lessons learnt' and identifying strategies to minimise the risk of a similar incident occurring in the future..."
AICD et al, 2022)
viii) remediation (despite the negative impact on the organisation, generally the customer has been the most compromised by the breach, ie loss of sensitive personal data; need to determine what support and/or compensation should be offered to those impacted; some vulnerable customers can become anxious, stressed and have an overwhelming sense of powerlessness and they need extra support, including financial compensation.
The response plan must be cascaded throughout the organisation so key staff sre aware of it and their roles and responsibilities; this needs to be regularly reviewed and updated based on changes in the threat environment, organisational structure, key digital assets, etc; need to keep hard copies of plans; each plan will be tailored to each organisation; need to continually test the response plan, ie 'rehearsals' and fine tune as required; these rehearsals need to be as realistic as possible, eg dealing with changing scenarios such as key systems compromised
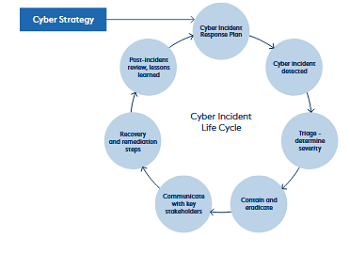
(source: AICD et al, 2022)
Areas of concern
- lack of formal documentation around the organisation's approach to cyber security
- limited understanding of the location of key digital assets and how they are protected plus who has access to them
- insurance can provides a false sense of security and generates complacency
- cyber strategy and risk controls are not subject to internal and external evaluations to allow periodic refinement related to evolving threats; these evaluations need to be impartial, genuinely independent and unfiltered by staff
- not understanding the cyber security capabilities of third party suppliers that support and manage the organisation's key assets and data, like software and IT infrastructure from cloud providers that are used to facilitate payment and invoicing processing, internal payroll, accounting services, customer databases word-processing software, etc
- poor internal cyber practices like weak password settings, lack of multi-factor authentication, etc
- not understanding third-party risk, ie for oversight in appointing and monitoring third-party suppliers that store and manage an organisation's key digital assets; need to have confidence and understanding of the key arrangements and controls used by a third party
- lack of data governance framework (including legislative requirements like privacy laws, etc) to guide how data is collected, held, protected and ultimately destroyed, ie life-cycle management of data (including secure destruction of all sensitive data whenever appropriate);
"...be aware of where, how and when data is collected by the organisation, its nature and volume, and where it is held, both by which providers and in which locations and for how long......To minimise the risk of data theft or loss, organisations should only collect and store the minimum amount of personal information that is legally required for its relevant services or operation......Data obtained for a legislative obligation is both stored in ......an encrypted and secure manner......and that data has also not been stored for 'other reasons' in the organisation..."
AICD et al, 2022)
- inadequate assessment of the organisation's internal cyber capabilities and maturity; for internal cyber capabilities, an organisation needs
"...An accurate understanding of key personnel competencies, reporting chains, responsibilities and the IT infrastructure essential for that business's operations (for example, databases, servers and cloud software), provides...... an overview of cyber security strengths, weaknesses and where enhancement is required. Internal cyber capability covers the following elements:
1. Adequacy of existing staffing, including the level of funding and the expertise of key cyber staff and the cyber knowledge of employees throughout the organisation
2. Existing infrastructure and systems, for instance the key software or operating systems utilised by customers and staff
3. The internal cyber control environment, for instance, the risk controls and reporting in respect of critical assets; and
4. Business continuity planning, covering how the organisation will respond in the event of a significant cyber incident..."
AICD et al, 2022
The aim is to enhance cyber capabilities, such as additional investments in new IT systems and infrastructure, etc that fits in with the organisation's broad strategic plan, ie
"...Doing so not only enhances cyber capability and resilience, but also has broader business benefits, such as improving reputation amongst stakeholders and maintaining a competitive advantage..."
AICD et al, 2022
Need to conduct benchmarking exercises (ideally using an external expert) against standard maturity models, frameworks, etc.
It is vital to continually review cyber strategy so that it remains 'fit-for-purpose' and robust; this includes identifying opportunities for improvement; learnings from pilot runs and cyber incidents (within and/or outside your organisation) need to be included in the strategy.
Some useful question:
"...1. Do you have a response plan informed by simulation exercises and testing?
2. What role does a board have in communications and/or public announcements?
3. In the event of data loss or theft, what is the plan for communicating with customers and employees?
4. Are you aware of your regulatory obligations to notify or report the incident?
5. Can you access external support it necessary to assist with the response?..."
AICD et al, 2022)
3. Embed cyber security into existing risk management practices (this involves
- understanding cyber risk is an operational risk that should be included in the approach to the organisation's risk management, ie need to be able to assess the interaction or impact of other risks on cyber and vice versa.
"...Risk controls or strategies are the mechanism by which an organisation seeks to avoid, mitigate or transfer cyber risk..."
AICD et al, 2022
How many lines of defence does your organisation have to handle a cyber attack? Normally, there are around 3 lines of defence.
For example,
"...the company detects the breach quickly. Internal teams execute the technical incident response playbooks to isolate and contain the impact. As it happens......implement the cyber incident plan, including advising key regulators..."
AICD et al, 2022
As transparency is key to member trust, remember to communicate promptly advising relevant stakeholders of the possibility that personal information was compromised; start a contact centre and introduce personalised support for impacted stakeholders; use external forensic experts to support your own staff's expertise.
NB Reduce the likelihood of cyber risk remaining the sole responsibility of IT or digital teams; it is a whole-of-organisation responsibility.
- as it is impossible to reduce the risk to zero, there are a number of accessible and low cost controls that are useful, such as patching and updating applications and antivirus software; only allow micro-settings from trusted sources, eg Microsoft; limit interaction between Internet applications and business systems; limit or restrict access to social media and external e-mail accounts; restrict use of USBs or external hard drives; restrict operating systems and software administrative privileges; implement multi-factor authentication; maintain off-line backups of key data; ensure that ex-staff no longer have access to systems and passwords.
NB Cyber risk appetite and profile
"...Cyber risk appetite......the risk that an organisation is willing to take in its digital activities to achieve its strategic objectives and business plans......cyber risk profile......commonly represents an organisation's 'point in time' position with respect to cyber risk once controls have been factored in..."
AICD et al, 2022
Cyber risk appetite has an impact on current and future business activities, overall strategic decision-making like investments, allocation of resources, etc; it is part of the organisation's holistic risk appetite.
"...A balanced cyber-risk appetite would recognise the inherent risk that comes with doing business in a digital economy, while taking a more pragmatic approach to managing this risk in the context of business opportunities..."
AICD et al, 2022
- internally assess the organisation's effectiveness of cyber controls to take into account changing threat environments, technology developments and the organisation's capability.
Areas of concern
- cyber risks not reflected in existing risk management frameworks and strategic decision-making
- lack of periodic reporting and regular engagement with staff on performance of risk controls
- not understanding the rapidly evolving nature of cyber risk
- lack of established metrics of cyber performance
- over-confidence that cyber risk controls are effective without regular external validation, ie 'what happened elsewhere with cyber threats, would not happen here'
- over-reliance on cyber security controls by key service providers, such as cloud software providers
- not assessing cyber security risks of potential vendors, ie procurement procedures for key goods and services
- not having secure and alternative back-ups such as an operating platform
- prolonged vacancies in key cyber staff roles
Some questions worth asking:
"...1. Does the organisation have a cyber risk appetite and is it being utilised in strategic decision-making?
2. Is cyber risk specifically identified in the organisations risk management framework?
3. How regularly does management present to the board or risk committee on the effectiveness of cyber risk controls?
4. For a larger organisation, is there external review or assurance of cyber risk controls..."
AICD et al, 2022)
4. Promote a culture of cyber resilience (this involves
- a proactive cyber strategy to identify business opportunities for the organisation to build cyber resilience; this involves governance decisions, oversight of cyber risk management, cyber control, etc
- regular and relevant training at all levels in the organisation to promote a cyber-resilient culture so that the organisation is vigilant about cyber threats; part of cyber-resilient culture involves creating a cyber security mindset and cyber literacy at all levels of the organisation; part of this involves knowing "...what data and systems are valuable, what types of cyber crises may need to be managed should the data be stolen or systems compromised, and can operations be restored in the event of an attack..."
AICD et al, 2022
- incentivise, ie link renumeration with cyber resilience measures, and promote strong cyber security practices like e-mail hygiene (avoid suspicious e-mail addresses, requests for information including pass words, login details, banking information, etc)
- understand that cyber resilience culture begins at the top, ie the board and senior management levels
Areas of concern
- not all staff undertake cyber security education nor participate in testing so don't realise where the risks lie
"...need to reinforce sound cyber hygiene practices and an overall culture of cyber resilience..."
AICD et al, 2022
- cyber security training is not implemented beyond the induction or orientation process new staff
- cyber security is not regarded as important as it is not reflected in job descriptions and KPIs (job performance)
- cyber risk is seen as an issue for only IT staff to manage
- not realising that frequently significant cyber incidents have an element of human error, eg an employee opening a malicious e-mail, staff working from home, etc
- communications do not reinforce the importance of cyber resilience to all staff, ie
"...cyber is seen as an issue only for front-line staff to manage..."
AICD et al, 2022
- there is a culture of 'exception' with regard to cyber hygiene and resilience
Some questions worth asking:
"...1. Is cyber security training mandatory across the organisation?
2. How often is training undertaken?
3. Is training differentiated by area or role?
4. How is the effectiveness of training measured?
5. What are the plans for building cyber security awareness?..."
AICD et al, 2022)
5. Plan for a significant cyber security incident (this involves
- all staff should proactively prepare and plan for a significant cyber incident; if done, the organisation
"...will be in a stronger position to mitigate impacts to its business operation, reputation and stakeholders, as well as recover in a timely manner..."
AICD et al, 2022
Need to be able to handle the spread of misinformation, especially via social media and the media in general; this requires preparation so there is a consistent approach to shaping the narrative, ie selecting the right people to respond in a constructive and measured way.
- use techniques like simulation, incident scenario testing, etc to build the organisation so all understand impacts, roles and responsibilities
- produce effective communications
"...clear and transparent communications with all key stakeholders during a significant cyber incident is critical in mitigating reputational damage and allowing for an effective recovery......Many organisations have experienced greater reputational damage from poor communications rather than the incident itself..."
AICD et al, 2022
However, sometimes assessing the full extent and severity of the cyber incident takes time; consequently, all key stakeholders must be continually updated as the situation evolves. Remember: the situation is evolving and what was communicated earlier may no longer be relevant; so stakeholders' expectations need to be managed.
- understand the regulatory requirements and obligations about handling an incident
- have a clear and transparent approach to communication with all key stakeholders, especially during a significant cyber incident - this is critical in mitigating reputational damage and allowing for an effective recovery
- 'to pay or not to pay?'; seek legal advice as paying a ransom does not guarantee your data is returned nor guarantee the organisation won't be subject to future attacks; see decision tree below:
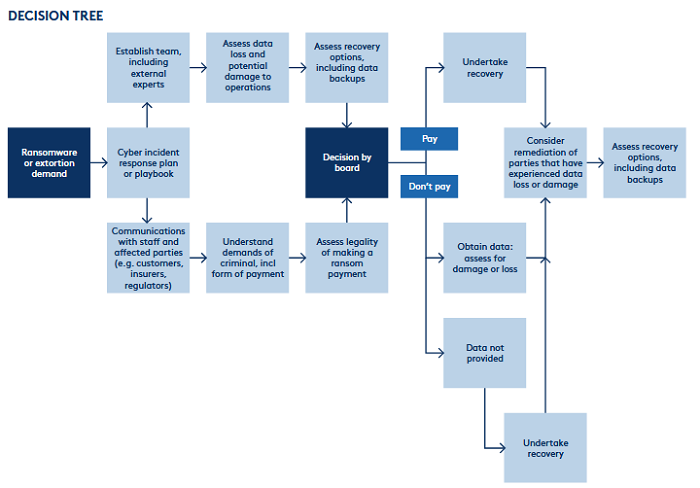
(source: AICD et al, 2022)
NB The decision tree represents a simple, linear and binary set of events and decisions from a particular form of data threat incident.
However, in reality situation is more complex and is based on imprecise, unreliable, fast-changing information or facts.
Areas of concern
- not understanding techniques like simulation, incident scenario testing, etc to test response plans
- not documenting lessons learnt from testing the strategy and using techniques like simulation, incident scenario testing, etc
- lack of clarity in communications in the event of an incident, ie public announcement need to be precise, especially when handling customers, suppliers, regulators, staff, etc
- not able to adequately handle the spread of misinformation, ie inaccurate or unverified information
NB Sometimes the perpetrators, or others impersonating them will spread misinformation to create confusion and profit opportunistically
- no post-incident review by relevant stakeholders
- lack of access to external expertise necessary to assist with response
- not appreciating the time it can take to restore the operating environment, including access to data that is critical for avoiding business failure.)
Post-incident review questions
"...1. What have you learnt from your existing systems in controlling cyber behaviour, including weaknesses?
2. Did everyone know their respective roles and follow them?
3. Did the organisation become aware of the incident within an appropriate timeframe? Was the incident reported to you by a third party such as a vendor or media? What does this tell you about monitoring and reporting controls?
4. Were the planned steps, responsibilities and procedures followed? Did these steps mitigate the impact of the incident?
5. Was the board appropriately briefed about the incident and did it have sufficient oversight and visibility of management actions?
6. What improvements could be made to the communications plan?..."
AICD et al, 2022
Summary
"...in general, management is responsible for developing, implementing and managing risk, controls. In larger organisations, a dedicated risk/audit/ technology committee allows directors to more closely oversee management. For smaller organisations, this oversight may occur in an informal manner, for example through conversations with key personnel..."
AICD et al, 2022
However, it is central to sound risk governance that all staff understand what cyber risks exist, what controls are in place to reduce or mitigate these risks, and how those controls are performing. Cyber-risk controls will ultimately depend on an organisation's size, complexity, information systems and infrastructure and cyber-risk appetite; irrespective of the size of an organisation, there are some commonalities.
NB
"...becoming cyber literate can help gain confidence in understanding the cyber threat landscape, potential impacts that cyber failings can have on the organisation, strategies for improving cyber resilience, as well as response and recovery in the event of cyber incidents..."
AICD et al, 2022
Remember:
"...Do the right thing and you can still be in trouble......Do not think your immune..."
John Mullins as quoted by AICD et al, 2022
Key Components of an effective cyber strategy
"...1. Governance Arrangements: promote effective governance of cyber security that is appropriate for the size and complexity of your organisation (Principle 1)
2. Identify and Protect: identify the key digital assets and data held by the organisation and how to comprehensively protect them (Principles 2 and 4)
3. Assess and Enhance: understand internal cyber capability, create a plan to enhance capability and promote a cyber resilient culture (Principles 2 and 4)
4. Detect, Respond and Recover: have plans and processes to detect cyber incidence and respond and recover effectively (Principal 5)
5. Monitor and Evaluate: report and up date.....to allow for ongoing assessment and refinement of the strategy (Principle 2)..."
AICD et al, 2022
Need to avoid, mitigate and transfer
- avoid (the risk by stopping or eliminating certain activities like collection and storage of unnecessary customer data)
- mitigate (reduce risk by implementing internal processes and/or utilising external service providers like multi-factor authentication, ensuring patching and anti-virus software is current and educate all staff about current cyber threats)
- transfer (transfer as much risk, including systems, infrastructure, functions, etc, as possible to external third parties).
Furthermore, all stakeholders need to be aware of behaviour and language, governance and incentives
- behaviour and language (ongoing cyber awareness training attended by all staff as part of continuous learning, rather than criticising staff; will improve understanding; using a common and accessible language when talking about cyber security; being open and honest about organisational cyber risk; encouraging all staff to play their role in promoting cyber resilience)
- governance (establish clearly defined roles, responsibilities for cyber security management; ensuring cyber security strategy and risk management are standing items on all meeting agendas; develop a comprehensive response plan in the event of a cyber security incident)
- incentives (develop KPI's and incentives for all staff; ensure cyber security performance, ie sound cyber risk management practices and execution of the cyber strategy; reward a proactive approach and transparency of attempted cyber breaches like phishing, etc.)
Ten key questions for:
A. roles and responsibilities
1. Do all levels of the organisation, especially the board and senior management, understand cyber risk well enough to oversee, manage and challenge?
2. Who has access to your key digital assets, ie can customer-facing staff have access and change the database?
cyber strategy
3. Who in your organisation has the responsibility for the management and protection of your key digital assets and data, ie decision-making and allowing third-party access like external suppliers?
4. Where, and with whom, are your key digital assets and data located and is this appropriate given the identified cyber risks?
B. cyber risk management
5. Is cyber risk specifically identified in the organisation's risk management framework and do you have adequate insurance coverage to cover any loss and/or compromise of your key digital assets?
6. How regularly do people who are responsible for cyber risk management report on the effectiveness of the cyber risk controls?
C. cyber resilient culture
7. Is cyber security training mandatory across the organisation and is differentiated by area or role?
8. How is the effectiveness of training measured, eg how often does training occur?
D. cyber incident planning
9. Do you have a cyber incident response plan, including a comprehensive communication strategy based on past experience (yours and other organisations), trial runs, etc?
10. Can you access external support if necessary to assist with a significant cyber security incident?
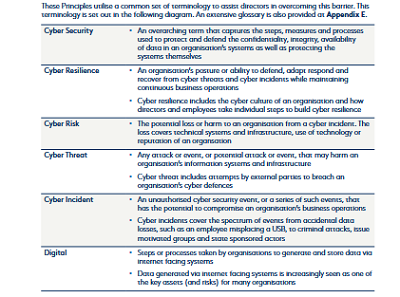
NB Terminology
(source: AICD et al, 2022)
